Access control systems are necessary to identify people in enterprises or other organizations and control access to facilities. Personal identifier with uniquecode (electronic key, magnetic card, chip-card or proximity card) is issued to every user of the system (all personnel of organization). When user wants to enter a room the user puts his or her identifier to the reader, which reads a code. Then reader sends the code to control module, which keeps in memory the list of codes that have access to the facility. If code that was read corresponds to any code in the list, control module gives signal to electronic door lock to open the door.

Electronic keys
Access control system based on electronic keys has the most efficient price/quality ratio. Electronic keys have exceptional reliability and extended life cycle, because chip (microchip that contains all personal data) is armored in a stainless steel can. Keys are not affected by magnetic fields, and have built-in unique security identifier number to exclude falsification.

- The longest lifecycle - 10 years warranty
- Chip is armored in a stainless steel can, therefore key is crash and waterproof
- Each key has built-in unique security identifier number to exclude falsification
- Power source protection
- Inexpensive reading devices
- High-speed reading
- Small size of the reader
- Possibility of outdoor operation

Magnetic cards as identification means are used worldwide. Majority of global payment systems use these cards to store information
Advantages of magnetic cards:
- Relatively low cost
- Possibility to print information on the surface of the card
- Possibility to use card's PIN code for additional security from fraudulent imitation

Proximity card is modern, prestige and easy-to-use identifier. Compared with magnetic card, lifecycle of the proximity card is much longer and they can work in extreme conditions, for example: on street, where humidity level is high, dust etc. Proximity reading of information makes use of access control system easier. It is especially important when reading distance is more than 10 cm. For example: if reader is based in car parking place, it is enough to reach one's hand out of car's window to identify oneself. In order to increase security and confidentiality, it is possible to embed scanning device into the wall. This option does not affect scanning quality.
- Each card has built-in unique security identifier number which excludes falsification
- It is easy to use proximity card - no contact with scanner is needed
- It is possible to embed scanner in the wall
- System can work in extreme conditions - on the street, in humid rooms etc.
- Possibility to print information on the card's surface

Security from outsiders
Access control system will guarantee safety of employees and facilities in organization. Only those people who have permission to enter or who are welcome will be able to enter the room. Outsiders will not disturb employees or endanger your property.

You can control personnel of your firm with access and security system. All actions of system users are registered in system journal. It is possible to monitor in real time dislocation of every employee and status of system devices (doors opened/closed, alarms on/off etc.). This feature makes easier work of guard and helps to monitor events in enterprise

You do not need different key for every door - you can quickly and easily open all doors, which you are allowed to open with the same identifier.

You can set up alarm for any room with the same key you open the door with. If there is room, which should not be accessible to other people during your absence, you can easily set up alarm when you go away and deactivate it when you come back.

Which access control system is most convenient for you depends on features of your enterprise (number of employees, number of rooms, and their dislocation) and tasks that system should perform.
ACT-2204 is simple access control system without a computer. This system consists of reader of identifier and control module which is installed for every door separately and it performs standard functions of the access control system - provides access control and possibility to set up alarm with the same identifier. We recommend ACT-2204 if:
- You have small number of system users (1-50)
- You have small number of rooms you want set up access control to (1-3)
- You do not need more than standard functions of the access control system

D`AACCESS is system that consists of identifier card reader and control modules that are united together in one system by special module - pre-processor. It gives you opportunity to receive different outputs and allows controlling personnel. We recommend D`ACCESS if:
- You have average or large number of system users
- You have average number of rooms you want set up access control to
- Additionally to access control you want to know when and what people have been in every room
- Guard should be able to see all system events on display (door is opened/closed, alarm is set up etc.)
- You want to know business hours of employees
D`ACCESS 2000 is system that consists of multiple sub-systems with one computer, which are connected together by access control server. It allows uniting in one access control system rooms that are located in different buildings. We recommend D`ACCESS 2000 if:
- You have large number of system users
- You have average number of rooms you want set up access control to
- You need the same system functions that are available in D`ACCESS
- Your enterprise is located in separate buildings and you want them to be united in one access control system
- You want to integrate your access control system with accounting system, security system or personnel system
SYSTEM WITHOUT A COMPUTER
ACT 2204 is simple access control system that controls access and organizes alarm system using electronic keys, magnetic cards and proximity cards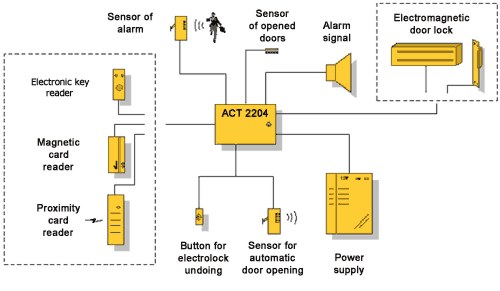
- use of one identifier (key) for access control and set up of alarm
- Various executive devices connectivity
- Alarm of control module cracking or unlocking of reader
- Quick programming with master-key programming of user right to set on/off alarm
- Door-open programmable interval
- Memory backup (essential when blackouts occur)
- Guard circuit and opened door alarm
- Power save operation mode
- Built-in electronic limit-switch of power consumption
Control module ACT 2204
ACT 2204 coordinates all other parts of system. It receives
electronic code from reader and signal if button for electronic-lock undoing is pressed,
if alarm sensor has detected offence or if door is opened. ACT 2204 process these signals
and if necessary opens door turns on alarm signal or some other device.
Reader
Reader is usually located outside door and person attaches identifier to it when he/she
wants to get inside the room. It reads electronic code from identifier and sends it to
control module, which checks whether owner of key has rights to access the room. Type of
reader depends on type of identifiers you use (electronic keys, magnetic cards, proximity
cards).
Electromagnetic door lock or
bolt
Electromagnetic door locks and bolts are devices that receive order from control module to
open door or barrier.
Button for electrolock undoing
This button is used to let inside person who is welcome but who does not have identifier
(visitor, client etc.). Usually button is located near office-girl work place so that she
can easily control which people she should let in.
Alarm sensor
If ACT 2204 is in alarm mode and alarm sensors detects offence (motion is room, attempt
knock out glass of window etc.), it sends signal to control module which turns on alarm.
Any NC/NO type alarm sensors can be used in system.
Sensor of opened doors
Sensor of opened doors detects whether doors are opened or closed at the moment. If person
has forgotten to close doors, sensor will signal to control module that doors are open and
after some time sound signal will be turned on. If door will be opened or smashed while
system is in alarm mode, sensor of opened doors will signalize to control module and alarm
signal will be turned on.
Alarm signal
Task of alarm signal is to inform person in charge (guard) about offence. ACT 2204 will
turn on alarm signal if:
- door is opened or broken while system is in alarm mode
- alarm sensor detects offence while system is in alarm mode
- reader is unplugged
- housing of control module is opened or smashed
is a new generation of access control systems based on modern technologies of data identification and transmission.
D’ACCESS is designed for sophisticated access control as well as for time attendance accounting at middle- and big-size companies with several departments branches) connected via LAN or WAN.
Our system allows to organize automated pass-points, to restrict access into private premises, to control employees’ presence inside company and to count working hours, as well as to generate reports on personnel truancies. It is also possible to integrate D’ACCESS with personnel management, accounting and EDP systems.
A choice of reports for departments sorted by many parameters (truancies, personnel early leaves, summarized and detailed day, week, month, quarter, year and/or any other period of time reports, alternative lists) can be generated by the system.
The system allows to determine tight working schedule for any employee (fixed, mixed, sliding, free, etc.), as well as allows to account overtime and night hours.
System implementation allows to increase internal security, personnel control and working efficiency many times, as well as allows to reduce staff.
Why Should Be Chosen?
- Creation of computerized security desk
- Employees’ photos depiction on a monitor of computerized security desk, when registering at a pass-point
- Registration of visitors
- Organization of transport pass-points
- Registering of documents like traveling and sick-lists, vacation orders, etc. for working hours’ accounting
- Registration of all user actions
- Unlimited quantity of keys and objects under control
- Unlimited distance between central management module and objects under control
- Unlimited quantity of automated working places
D'ACCESS has the following advantages :
- Does not need additional communication lines – it uses existing LAN or WAN for communication;
- It is possible to integrate D’ACCESS with systems from other vendors, including personnel, accounting department, as well as EDP and management system;
- Easily upgradeable and expandable according to expanding size of company;
- Any language chosen (e.g. Latvian, English, Russian etc.).
Architecture
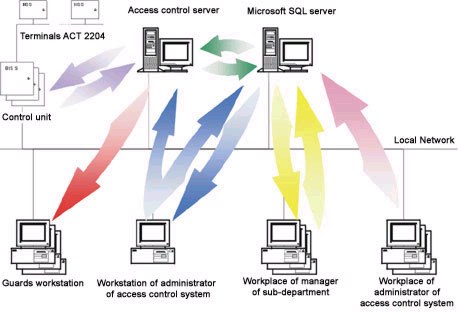

The system consists of the following basic modules:
- Access control server – central module of system management;
- Automated working places (AWP) of pass-bureaus to issue personal electronic passes with certain access rights;
- AWP for department reports on working hours of personnel access to controlled premises;
- AWP of security department to register visitors, control turnstiles etc.;
- AWP of system administrator – for management and maintenance.
Technical
Specifications
The system has a modular structure and it is able to work on stand-alone PC or PC LAN. In
addition, a necessary number of working places can be arranged (e.g. a manager of every
department is able to look through reports on his employees’ working hours).
All basic modules can be interconnected through LAN, Internet or any other communication
media that supports TCP/IP protocol. This assures centralized management of subdivisions
and remote objects.
Any mixture of electronic keys, smartcards, and magnetic or wireless cards can be used as
passbooks. The system is functioning in MS SQL Server environment. All program modules are
running under Microsoft Windows